On February 13, 2026, the U.S. Department of Health and Human Services (“HHS”), Office for Civil Rights (“OCR”) announced its civil enforcement program to implement the updates to the Substance Use Disorder (“SUD”) confidentiality provisions of the regulation at 42 CFR Part 2 (“Part 2”).1 The new enforcement program became effective February 16, 2026, in accordance with the deadline set by the 2024 Final Rule modifying Part 2 (“2024 Final Rule”).
Continue Reading HHS OCR Announces Civil Enforcement Program for Confidentiality of Substance Use Disorder Patient Records
Supreme Court to Consider the Video Privacy Protection Act
Last week, the U.S. Supreme Court agreed to hear a case that is expected to resolve a long-developing split among federal courts of appeals over the scope of the Video Privacy Protection Act of 1988 (“VPPA”), 18 U.S.C. § 2710. In granting certiorari in Salazar v. Paramount Global, the Court will address a question that has increasingly shaped VPPA class action litigation in recent years: who qualifies as a “consumer” protected by the statute.
Continue Reading Supreme Court to Consider the Video Privacy Protection ActOn the Twelfth Day of Data… Privacy Litigation: Four Notable Developments From 2025

The past year was a busy one for privacy litigation: Website tracking litigation gained momentum. Plaintiffs repurposed legacy wiretap and video privacy statutes to target pixels, chat bots, and other AI-enabled user tools. Courts issued decisions that altered liability theories and deepened splits over statutory terms and defenses. Regulators remained active and staked out positions that stand to adjust private-plaintiff approaches to routine commercial website tracking.
In this post, we distill the year’s most consequential developments and what they mean for 2026.
Continue Reading On the Twelfth Day of Data… Privacy Litigation: Four Notable Developments From 2025On the Eleventh Day of Data… Unwrapping DSARs in 2026

As the year draws to a close, reform of the data subject access request (DSAR) regime in the EU and the UK may turn out to be a welcome gift for organisations grappling with complex access requests. Regulators in both jurisdictions are signalling a more flexible, pragmatic approach to compliance, recognising that DSARs have often been exploited for tactical or disruptive ends.
Continue Reading On the Eleventh Day of Data… Unwrapping DSARs in 2026On the Tenth Day of Data… Looking Back at 2025 and Ahead to NYDFS Enforcement Priorities in 2026

While 2025 may have brought questions about the level of enforcement we would see from federal regulators, there was no question that state regulators would continue to be active, especially in the financial privacy space. In 2025, we saw the New York Department of Financial Services (NYDFS) implement the final phases of amendments to its NYDFS Cybersecurity Regulation (23 NYCRR Part 500) that originally passed back in 2023 (see our earlier post on the amendments here). The final implementation phases milestones came as scheduled in May and November 2025, and just days before the final set of requirements took effect on November 1, NYDFS also issued new industry guidance on managing third-party risks. Taken together, the guidance and final amendments underscore what NYDFS will be scrutinizing in upcoming investigations and examinations: leadership oversight and documentation, complete asset inventories governed by clear policies, strict access controls and privilege management, universal multi-factor authentication coverage or well‑justified compensating controls, and credible third‑party risk management evidence.
Continue Reading On the Tenth Day of Data… Looking Back at 2025 and Ahead to NYDFS Enforcement Priorities in 2026On the Ninth Day of Data… State of the States: This Year’s Key Privacy Law Developments Across the U.S. States

The continued absence of a comprehensive federal privacy law once again positioned state legislatures as the primary forces behind data privacy developments in the U.S. this year. In 2025, eight new comprehensive state privacy laws took effect, adding to a growing patchwork of regulations that now spans 20 states. These laws generally reinforce established standards but introduce some important differences in applicability, exemptions, and sensitive data protections, making multi-state compliance increasingly complex.
States also continued to refine their data breach notification requirements, with notable amendments in New York, California, and Oklahoma aimed at strengthening consumer protections and reporting standards. Meanwhile, the rapid proliferation of state-level AI legislation—alongside a controversial new executive order directing federal agencies to challenge such laws—added a new layer of considerations for businesses leveraging artificial intelligence. With additional privacy laws set to take effect in 2026 and even stricter proposals on the horizon, organizations should remain proactive in adapting to this dynamic and increasingly fragmented regulatory environment.
Continue Reading On the Ninth Day of Data… State of the States: This Year’s Key Privacy Law Developments Across the U.S. StatesOn the Eighth Day of Data… AI Regulation – A 2025 Recap and a Look Ahead to 2026

In 1950, reflecting on the future of machine intelligence, Alan Turing observed: “We can only see a short distance ahead, but we can see plenty there that needs to be done.” With several large language models, most notably OpenAI’s GPT-4.5, passing the Turing Test in 2025, some governments have taken steps towards stricter regulation this year, with others still working to determine what “needs to be done” for AI regulation in the year ahead.
Most notably, this year saw key provisions of the EU AI Act—the world’s first comprehensive AI-dedicated law—take effect. However, instead of seeing the “Brussels effect” with AI regulation, going into 2026, the global approach appears to be leaning towards that of the UK and U.S., which have led the charge for a looser regulatory environment in recent years.
Continue Reading On the Eighth Day of Data… AI Regulation – A 2025 Recap and a Look Ahead to 2026On the Seventh Day of Data… The Growing Pains of Regulation S-P in 2025

Financial regulators including the Securities and Exchange Commission (“SEC”) continued to focus on data protection and cybersecurity issues throughout 2025. With the amendments to the Safeguards Rule and Disposal Rule of Regulation S-P officially taking effect, the SEC is continuing to assert a more prominent role in data protection, a trend that will undoubtedly continue and likely expand throughout 2026.
Continue Reading On the Seventh Day of Data… The Growing Pains of Regulation S-P in 2025On the Sixth Day of Data… CISA, CIRCIA, and the Future of Critical Infrastructure Security

This holiday season—following a year of headline breaches, surging supply-chain attacks, and major regulatory changes—cyber resilience tops every corporate wish list.
The Cybersecurity and Infrastructure Security Agency (“CISA”) remains at the forefront of U.S. cybersecurity amid a turbulent year of leadership change and policy realignment. With the long‑awaited Cyber Incident Reporting for Critical Infrastructure Act (“CIRCIA”) rules slated for May 2026 and a continuing focus on international cyber strategies, the agency is poised to shape the future of critical infrastructure security. CIRCIA will introduce mandatory cyber incident and ransomware payment reporting for covered critical infrastructure, driving faster federal response and shaping compliance programs, contractual obligations, and risk governance across sectors. At the same time, CISA’s 2025–2026 International Strategic Plan outlines the federal government’s purported approach to cross‑border cyber defense—prioritizing partnerships, information sharing, and supply‑chain risk mitigation—with direct implications for transnational firms. Yet CISA faces major challenges, including leadership gaps, workforce constraints, and increased political scrutiny, that may threaten its ability to fulfill its mission in the year ahead.
Continue Reading On the Sixth Day of Data… CISA, CIRCIA, and the Future of Critical Infrastructure SecurityOn the Fifth Day of Data… Reflections and Compliance Advice on the DOJ’s Data Security Program
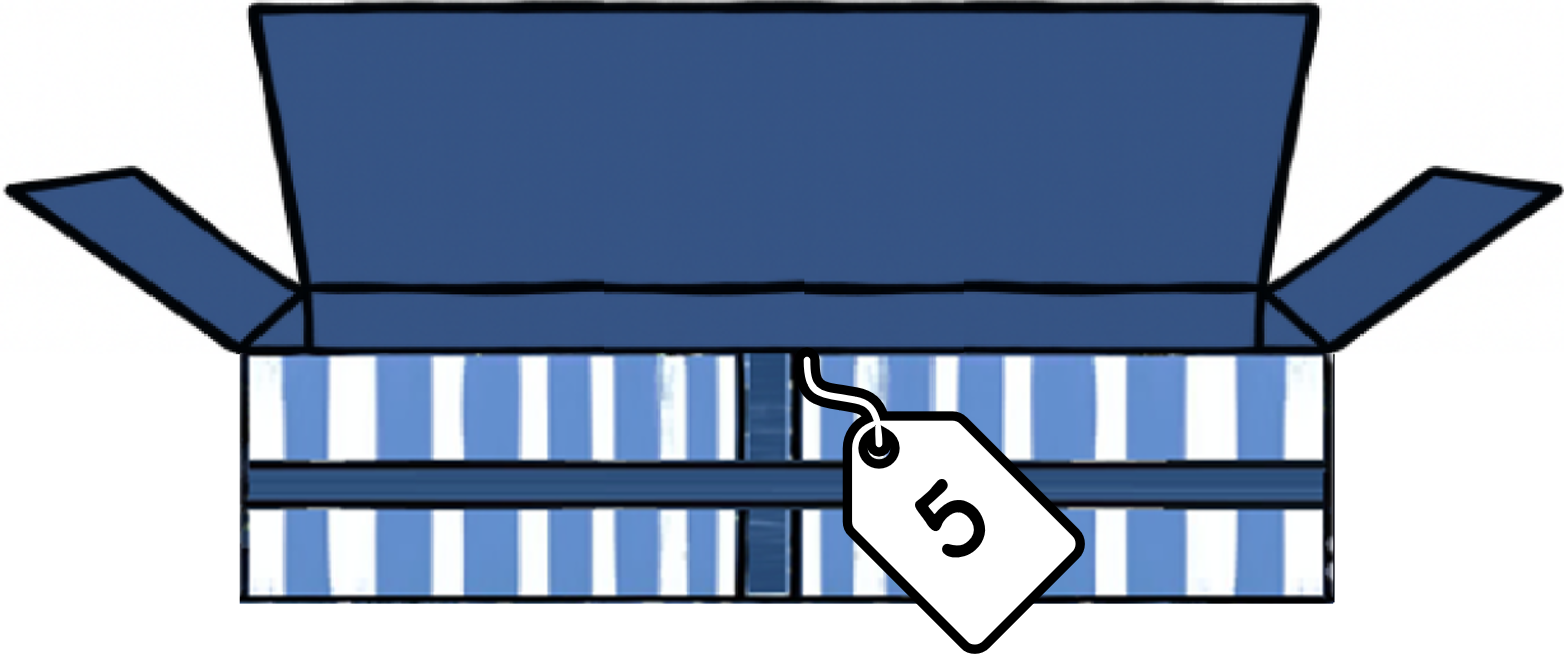
As compliance professionals reflect upon the past year, many will look back with frustration on efforts taken to comply with the Department of Justice’s Data Security Program (the “DSP” or “Rule”). Not because the efforts taken were in vain, but because the DSP is one of the most complicated, amorphous, far-reaching, yet impactful U.S. government regulations in recent memory. Any organization that collects or has access to U.S. sensitive personal data—regardless of whether that data is anonymized, pseudonymized, de-identified, or encrypted—should be assessing its compliance with the DSP. In other words, nearly every organization in the U.S. and many outside the U.S. fall under the Rule.
Continue Reading On the Fifth Day of Data… Reflections and Compliance Advice on the DOJ’s Data Security Program